As I mentioned in one of my previous posts about tools for Dynamic Malware Analysis, CaptureBat is a very essential tool for this purpose. This tool shows us verbose output of the things happening at the registry, file and processes level.
Starting off with Capture Bat
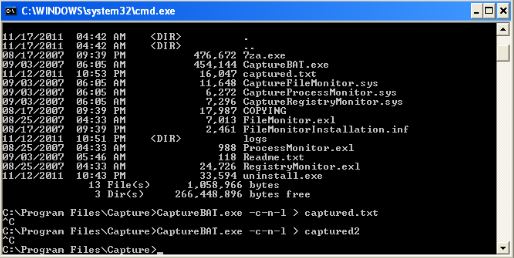
One of the easiest ways to go through the information captured by this tool is to copy the output in a text file for easy reference
But this limits the overall efficiency as it can geta little cumbersome to go through the captured data of a malware which was running for about 5 minutes or so. Its always good to have a way in which we can categorize, search and filter the contents to our liking. Guess what, we already have a way...Excel.
Efficiency through Excel
We can export the captured data into an excel sheet and take benefit of the excellent filtering capabilities. T start off, simply capture the data in a normal CaptureBat file and import it into excel.
When Importing into Excel choose file type as 'Delimited'.
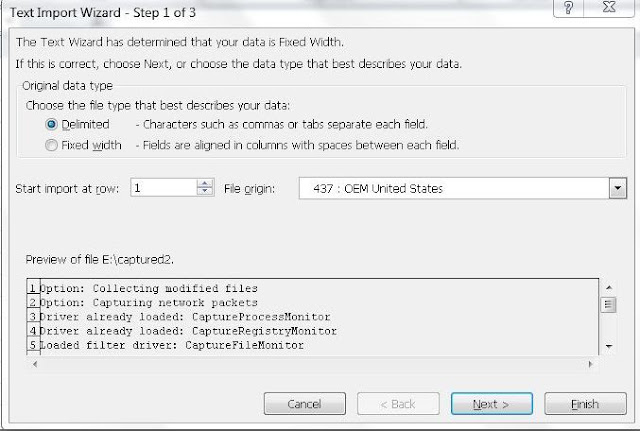
As of now I have observed that choosing the options 'Tab', 'Space' and ':' in 'Other' works best for me.
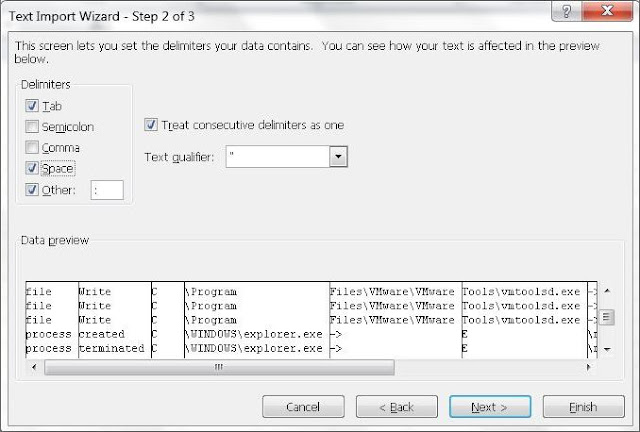
Once done, we get the output in an Excel as shown below.
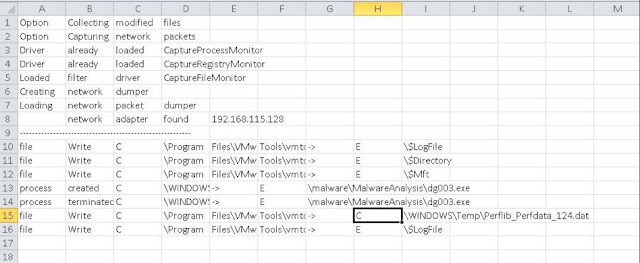
We can use filters to narrow down on the type of operation we want to check. For instance we can choose to only see the 'write' operations performed.
Starting off with Capture Bat
One of the easiest ways to go through the information captured by this tool is to copy the output in a text file for easy reference
But this limits the overall efficiency as it can geta little cumbersome to go through the captured data of a malware which was running for about 5 minutes or so. Its always good to have a way in which we can categorize, search and filter the contents to our liking. Guess what, we already have a way...Excel.
Efficiency through Excel
We can export the captured data into an excel sheet and take benefit of the excellent filtering capabilities. T start off, simply capture the data in a normal CaptureBat file and import it into excel.

When Importing into Excel choose file type as 'Delimited'.

As of now I have observed that choosing the options 'Tab', 'Space' and ':' in 'Other' works best for me.

Once done, we get the output in an Excel as shown below.

We can use filters to narrow down on the type of operation we want to check. For instance we can choose to only see the 'write' operations performed.

