You can get the Trojan on Contagion Malware Dump site
http://contagiodump.blogspot.com/2011/03/take-sample-leave-sample-mobile-malware.html
Direct Link
http://www.mediafire.com/?z4296jczsx4jc3d
Another trigger point is specific messages sent to the app. There are four such cases
Case I : String "formula401"
http://contagiodump.blogspot.com/2011/03/take-sample-leave-sample-mobile-malware.html
Direct Link
http://www.mediafire.com/?z4296jczsx4jc3d
Begin by renaming the .apk file to a zip file. This gives access to the contents of the .apk file.
We can see the classes.dex file.
Let’s use Dex2Jar on the Classes.dex file to get access to the application code.
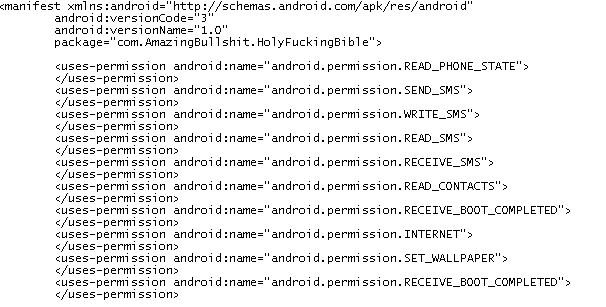
Don’t start exploring the code as yet. It is always better to have the AndroidManifest.xml file handy when exploring the code. So let’s get it using AXMLPrinter.
Its always better to have a look at the AndroidMannifest.xml file to start with. It gives an idea what kind of permissions the app is asking from the user.
The manifest file for the current app indicates a few interesting things.
The app has requested permissions for the following
Read and send Sms
Access Contact information
Understand when the device boots
Set wallpaper
Its always good to have an eye open for components or modules mentined in the manifest file and check the workings of that module in the class files
For instance, receiver android:name="com.YahwehOrNoWay.PostingServiceReceiver" which we see in the manifest file can also be seen in the code obtained from the .dex file.
If we inspect the code closely we can see that the app keeps a check on when the device boots itself. Perhaps it triggers something when the app boots?
Looking at the manifest file gives a feeling that the component ‘YahwehOrNoWay’ will have a lot of juicy stuff. Let’s explore it more in the code.
The app is creating a service named ‘theword’. This would keep running in the background and probably monitor the device for trigger events.
If we inspect the code below, it gives an indication that the app runs its operations at fixed time intervals.
Close inspection of another piece of code gives an indication of another trigger point.
localStringBuilder1.toString().matches("05212011"))
This indicates that the date 21/05/2011 is a trigger event for this particular app. If you have been following the news this date has been prophesized to be **drum rolls** The day the world ends (again). It was stated by radio host Harold Camping that this day marks the Rapture and Judgement Day. This is another indication of how much the malware writers use Social Engineering.
Another trigger point is specific messages sent to the app. There are four such cases
Case I : String "formula401"
This commands instructs the trojan to send contact information to a file hosting site 'turbobit'.
Case II: String "pacem"
This command instructs the trojan to send a download recommendation to all contacts on the phone.
Case III: Date is 05/21/2011
The trojan creates a database mydb.db when it detects that the date is 21 May 2011.
It adds some values to the database and sends these values as a reply whenever an SMS is sent to the device
I wanted to show this behavior in real time on two simulators but sadly this behavior was not being replicated. I will surely try again and update.
Also, the wallpaper is changed as shown in the code below
Case IV: Date is 05/22/2011
The trojan replies a message 'Looks like Jebus is a no show, maybe Judaism was on to something' to any SMS received by the device.
Also, the wallpaper of the device is changed as shown in the following code.
As you can see the trojan is fairly capable of many things, most prominent includes sending vital information about the contacts present in the phone to the author thereby stealing sensitive information. Also the trojan spreads by enticing people present in the contact list to download the same app thereby spreading even more.
Case II: String "pacem"
This command instructs the trojan to send a download recommendation to all contacts on the phone.
Case III: Date is 05/21/2011
The trojan creates a database mydb.db when it detects that the date is 21 May 2011.
It adds some values to the database and sends these values as a reply whenever an SMS is sent to the device
I wanted to show this behavior in real time on two simulators but sadly this behavior was not being replicated. I will surely try again and update.
Also, the wallpaper is changed as shown in the code below
Case IV: Date is 05/22/2011
The trojan replies a message 'Looks like Jebus is a no show, maybe Judaism was on to something' to any SMS received by the device.
Also, the wallpaper of the device is changed as shown in the following code.
As you can see the trojan is fairly capable of many things, most prominent includes sending vital information about the contacts present in the phone to the author thereby stealing sensitive information. Also the trojan spreads by enticing people present in the contact list to download the same app thereby spreading even more.